Enterprise Mobility Security Essentials
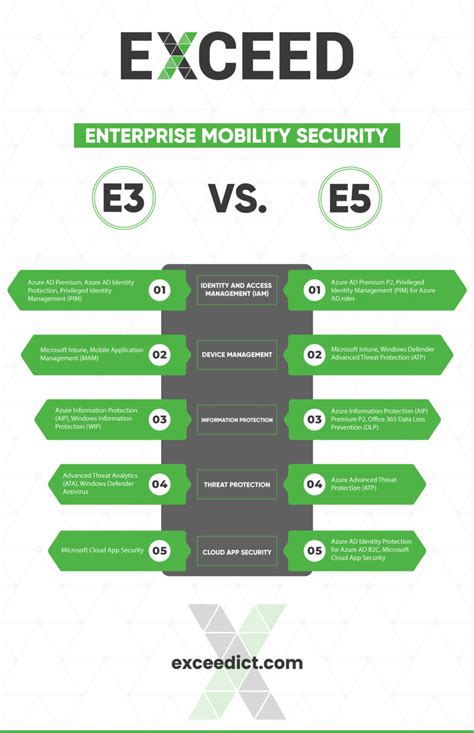
As the world becomes increasingly digital, enterprises are embracing mobile technologies to enhance productivity, improve customer engagement, and stay competitive. However, this shift towards mobility also introduces new security challenges that can put an organization's sensitive data and reputation at risk. In today's fast-paced, digitally driven business landscape, understanding enterprise mobility security essentials is crucial for safeguarding against threats and ensuring the continuity of operations. With the average cost of a data breach exceeding $3.9 million and the number of mobile devices in the workplace expected to continue rising, implementing robust security measures is not just a recommendation, but a necessity.
The bring-your-own-device (BYOD) policy, which allows employees to use their personal devices for work, has become a common practice in many organizations. While BYOD increases flexibility and employee satisfaction, it also expands the attack surface, making it harder for IT departments to maintain control and security over the devices accessing the corporate network. Furthermore, the diversity of devices, operating systems, and applications used in a BYOD environment complicates the implementation of uniform security policies. For instance, a study by Cisco found that 71% of organizations allow personal devices in the workplace, yet only about 48% of these organizations have the necessary security controls in place to protect against mobile threats.
Primary Enterprise Mobility Security Concerns

Several primary concerns need to be addressed when it comes to enterprise mobility security. First and foremost is the protection of sensitive data. With employees accessing and transmitting corporate data on their mobile devices, there’s a heightened risk of data breaches due to lost or stolen devices, unauthorized access, or malicious apps. According to a report by IBM Security, the average time to detect and contain a breach is 280 days, emphasizing the need for proactive security measures. Another significant concern is the vulnerability of mobile devices to malware and other cyber threats. Mobile malware can compromise device security, leading to unauthorized data access, eavesdropping, or even the hijacking of devices for malicious activities like botnets.
Security Measures for Enterprise Mobility
To combat these risks, enterprises can implement several security measures. Mobile Device Management (MDM) solutions are crucial for enforcing security policies, managing applications, and protecting data on mobile devices. MDM allows IT to remotely wipe data from lost devices, enforce encryption, and ensure that only approved applications are installed. Additionally, Mobile Application Management (MAM) focuses on managing and securing the applications themselves, without requiring control over the entire device. This approach is particularly useful in BYOD environments where employees might be reluctant to enroll their personal devices in an MDM solution.
| Security Measure | Description |
|---|---|
| MDM | Mobile Device Management for overall device security and policy enforcement |
| MAM | Mobile Application Management for securing and managing mobile applications |
| EMM | Enterprise Mobility Management, combining MDM and MAM with additional security features |
Data Protection Strategies

Protecting sensitive corporate data is at the heart of enterprise mobility security. This involves encrypting data both in transit and at rest, using technologies like SSL/TLS for data transmission and AES for data storage. Implementing a secure authentication process, such as multi-factor authentication (MFA), adds an additional layer of protection against unauthorized access. Moreover, deploying mobile-specific security solutions, such as mobile threat detection (MTD) and mobile security information and event management (SIEM) systems, can help in identifying and mitigating mobile-specific threats in real-time.
Best Practices for Mobile Application Security
When it comes to mobile applications, security should be a primary concern from the development stage onwards. Secure coding practices, regular security audits, and penetration testing can help in identifying and fixing vulnerabilities before the application is deployed. Additionally, ensuring that applications are updated regularly with the latest security patches is crucial. The use of Transport Layer Security (TLS) for secure data transmission and code obfuscation to protect against reverse engineering can further enhance application security.
Key Points
- Implementing robust MDM/MAM solutions to manage and secure mobile devices and applications
- Utilizing EMM solutions for a comprehensive approach to mobility security
- Protecting sensitive data through encryption, secure authentication, and mobile threat detection
- Adopting secure coding practices and regular security audits for mobile application development
- Staying informed about the latest mobile security threats and trends to adjust security strategies accordingly
In conclusion, enterprise mobility security is a multifaceted challenge that requires a strategic and comprehensive approach. By understanding the primary concerns, implementing robust security measures, and adopting best practices for data protection and mobile application security, organizations can significantly reduce the risks associated with mobile technologies. As the mobile landscape continues to evolve, staying informed and adapting security strategies to address new threats and technologies will be essential for protecting enterprise assets and ensuring business continuity.
What are the primary security concerns for enterprise mobility?
+The primary security concerns include protecting sensitive data, preventing malware and cyber threats, and ensuring the security of mobile devices and applications.
How can enterprises protect their data in a mobile environment?
+Enterprises can protect their data by implementing encryption, secure authentication processes, and utilizing mobile-specific security solutions such as mobile threat detection and SIEM systems.
What role does MDM play in enterprise mobility security?
+MDM (Mobile Device Management) plays a crucial role in enforcing security policies, managing applications, and protecting data on mobile devices. It allows for remote wipe, encryption enforcement, and ensures only approved applications are installed.



